Add Secrets via GCP Secret Manager
In order to protect sensitive information such as API keys and Secret keys from being exposed or misused, it is important to securely store them.
One way to achieve this is by using Google Cloud Platform (GCP) Secret Manager. By adding secrets to GCP Secret Manager, you can easily manage and securely access them when needed.
While writing cloud functions via Derivatives, Extensions, Actions, and Webhooks, you can leverage the GCP Secret Manager to add and utilize secret keys seamlessly.
Steps to Set Up Secrets
Step 1: Retrieve your API Keys
Before adding secrets to GCP Secret Manager, ensure you have the API keys you wish to add. These can be obtained from the respective services or platforms you are integrating with.
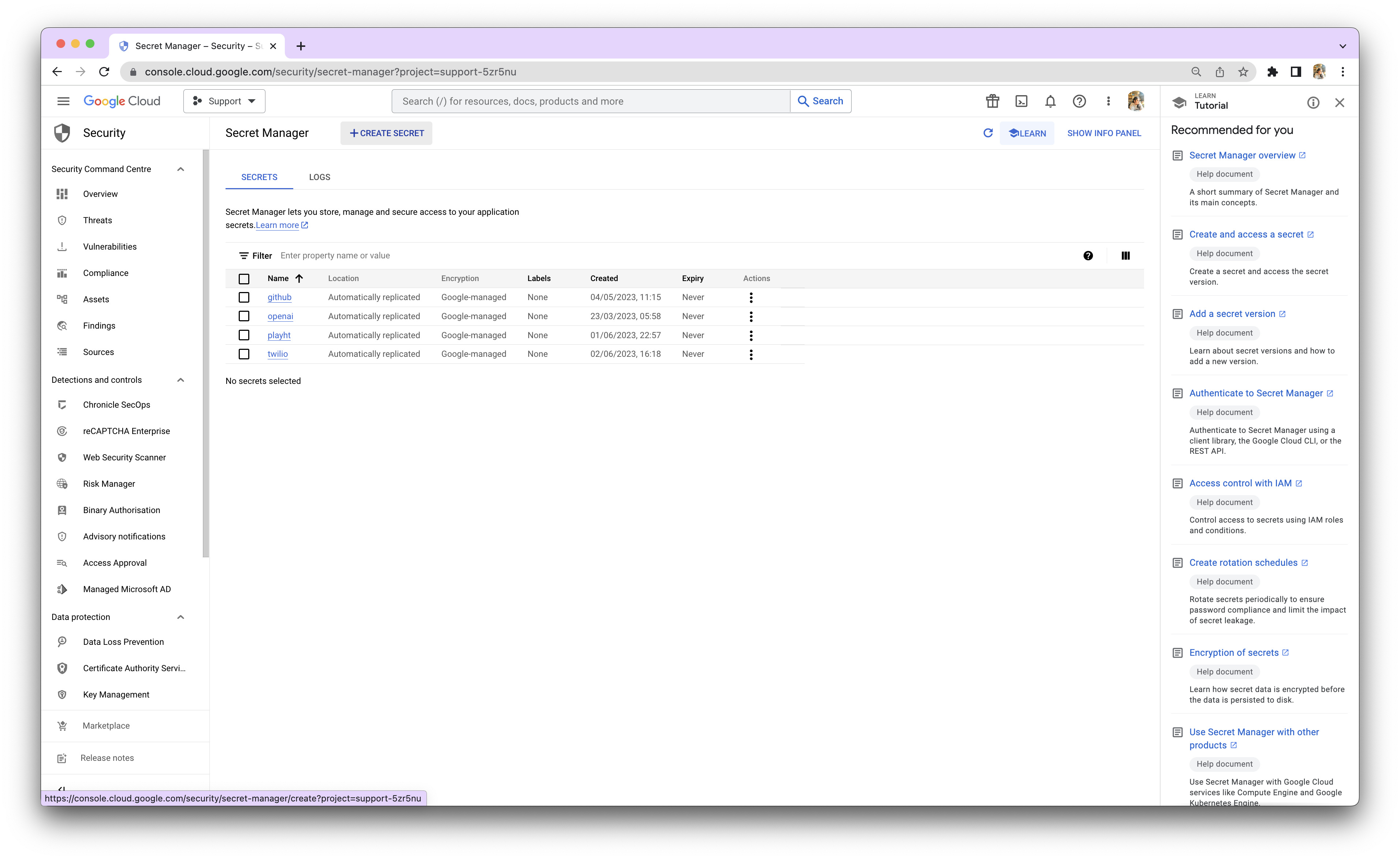
Step 2: Access GCP Secret Manager
Go to the GCP Secret Manager console by visiting https://console.cloud.google.com/security/secret-manager. Make sure you are logged in to your Google Cloud Platform account.
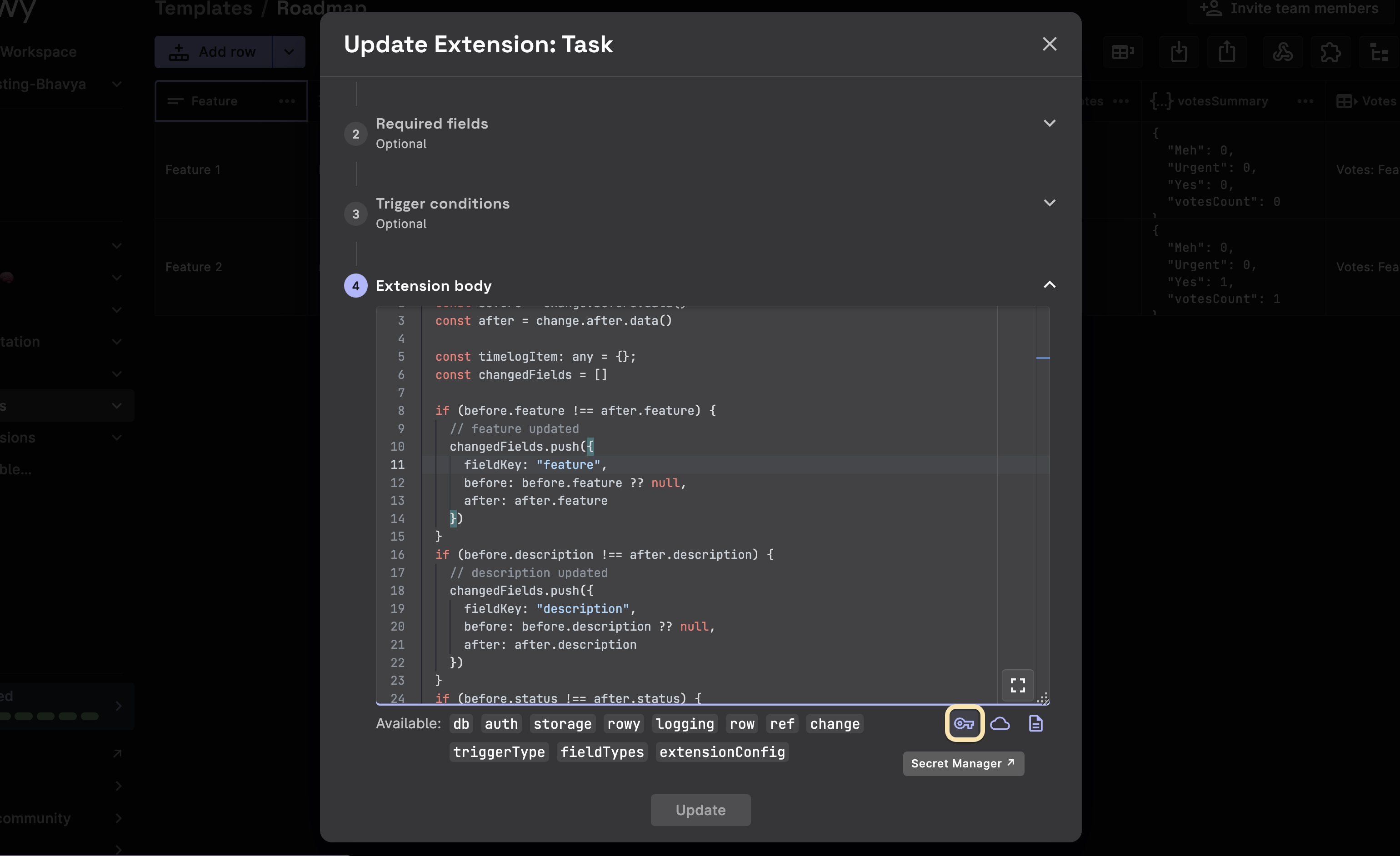
Easy Access to the Secret Manager via Rowy
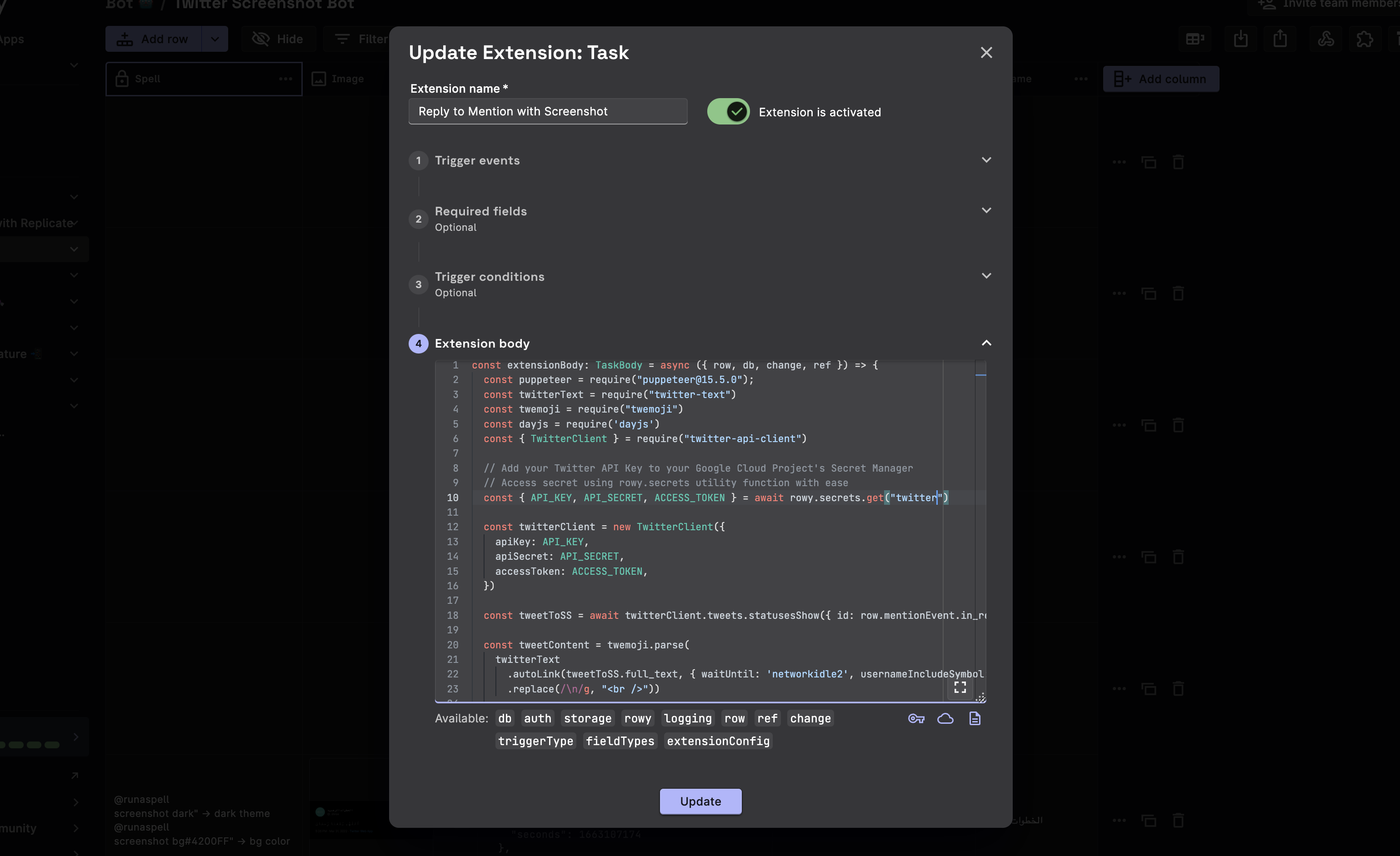
You can also access the GCP Secret Manager dashboard directly when editing the scripts. Click on the Key Button 🔑 below the code editor to open the GCP Secret Manager console. This will help you to add Secrets as you write code without having to navigate and switching tabs.
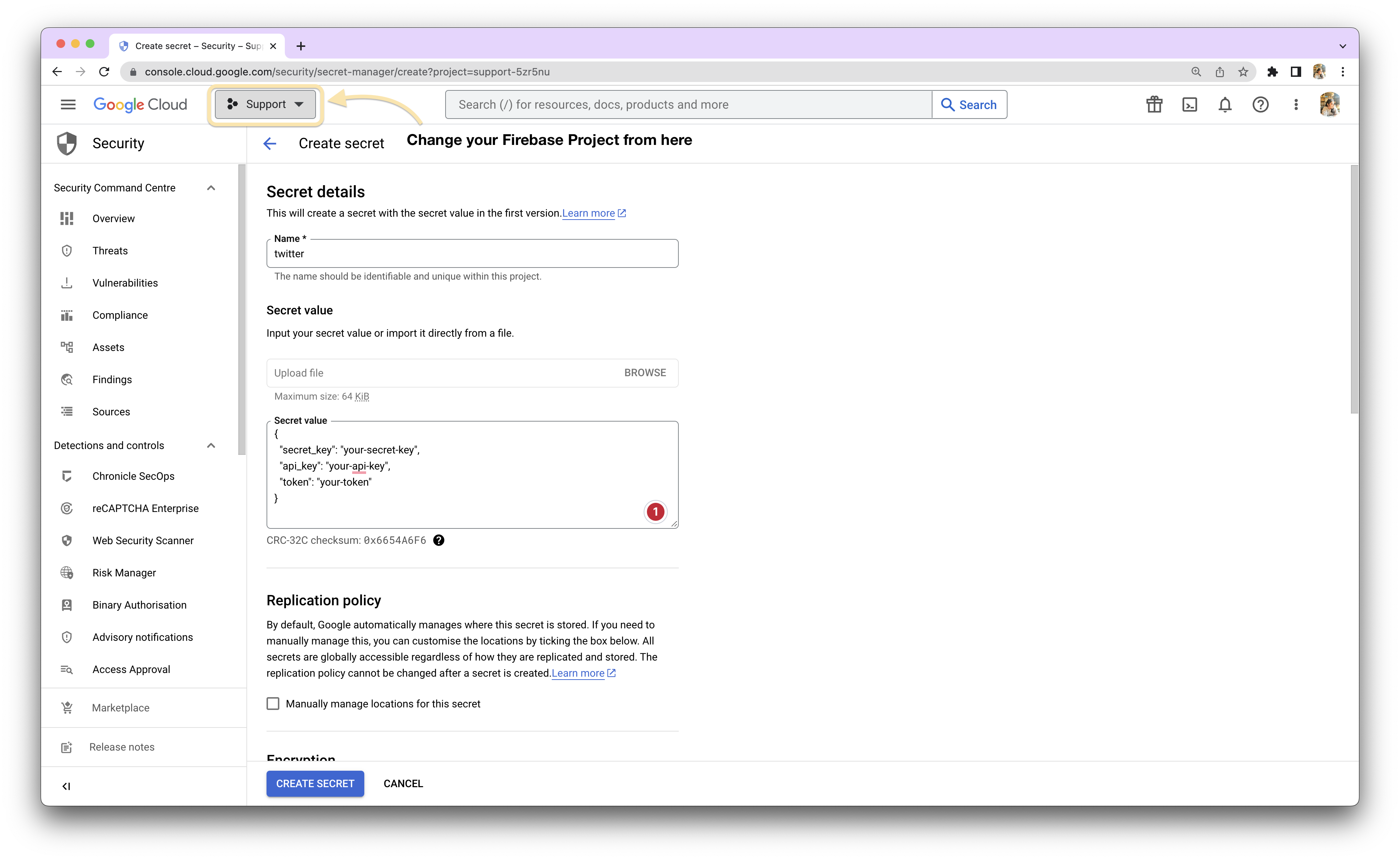
Step 3: Add Secret Name
In the GCP Secret Manager console, click on "Create Secret". Provide a meaningful name for your secret. This name will be used to reference the secret when accessing it programmatically.
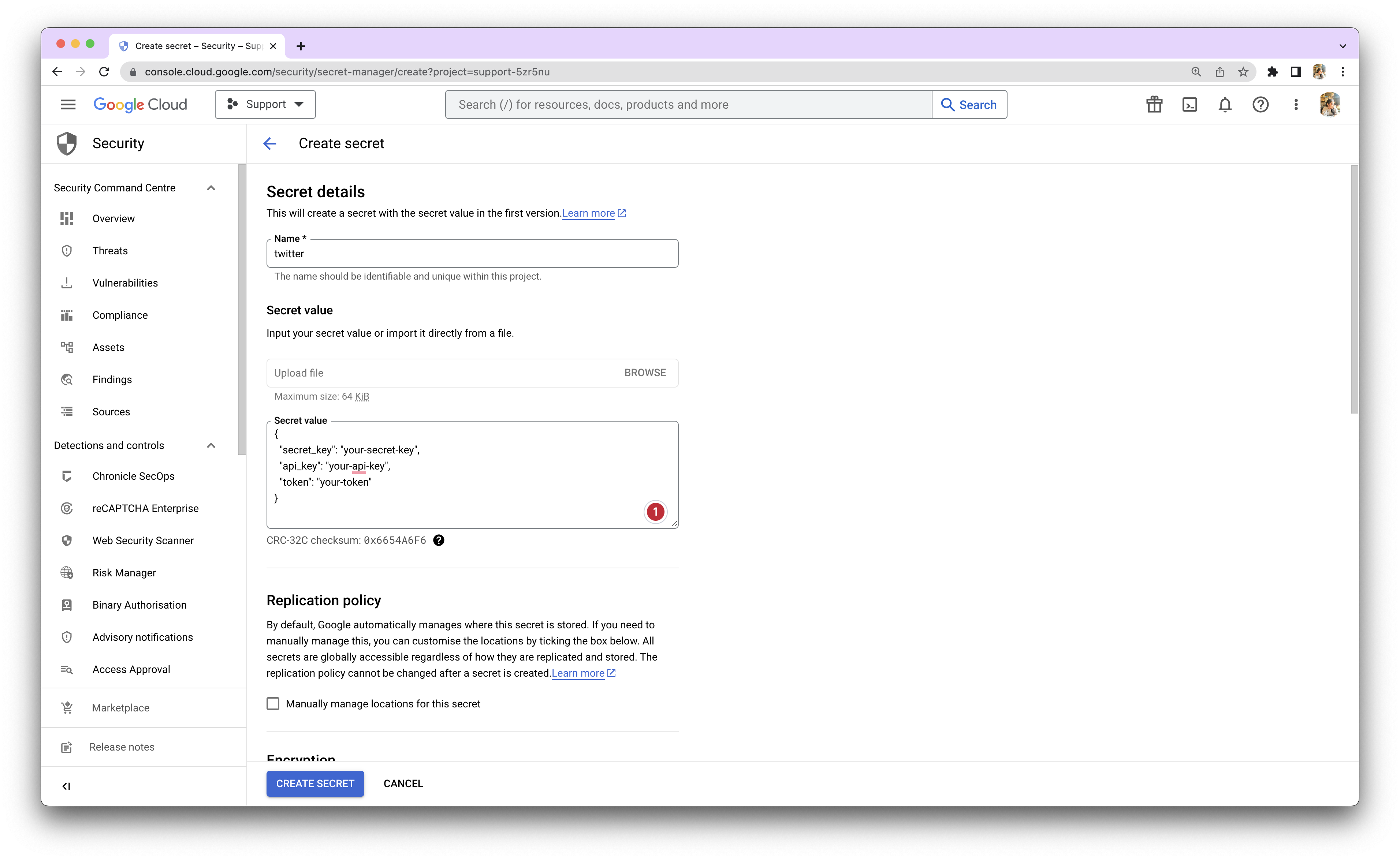
Step 4: Add Secret Value
Depending on your requirements, you can either paste the key directly or store multiple keys using a JSON object.
If you have a single key, paste it into the provided field. If you have multiple keys, you can create a JSON object to store them. For example, if you have a Secret Key, API Key, and a Token for Twitter, your JSON object might look like this:
{
"secret_key": "your-secret-key",
"api_key": "your-api-key",
"token": "your-token"
}
Step 5: Create the Secret
After adding the secret value, click on "Create" to store the secret securely in GCP Secret Manager. The secret is now ready to be accessed.
Accessing Secrets in Rowy
To use the secrets you added via GCP Secret Manager in Rowy, you can access them using the following code snippets:
Step 1: Accessing a Single Secret
const secretValue = await rowy.secrets.get("SECRET_NAME");
Replace SECRET_NAME with the actual name of the secret you created in GCP Secret Manager. The secretValue variable will contain the value of the secret.
Step 2: Accessing Multiple Secrets
const { api_key, secret_key, token } = await rowy.secrets.get("twitter");
Replace "twitter" with the actual name of the secret containing the JSON object storing multiple keys. The variables api_key, secret_key, and token will contain the corresponding values from the JSON object.
Adding Secrets to the Correct Project
Ensure that you add the secrets in the correct project on the Google Cloud Platform. This will ensure that the secrets are accessible to the Rowy environment and avoid any confusing errors.